Looking to download your own copy of the FortiGate config leaks? I’ve mirrored it here for free!
I was catching up on some InfoSec news from the week and read Hackers leak configs and VPN credentials for 15,000 FortiGate devices, then decided I’d like to check out a copy of the Belsen Group leak for myself. It’s not often you get to see in-the-wild configuration, passwords, etc. for anything ranging from small businesses to major enterprises.
While I started a download for the original data from Belsen Group’s onion site (cheers to @GossiTheDog’s thread), I looked around to see if there was anyone who’d mirrored a copy already.
Color me unsurprised to find an attacker trying to get InfoSec professionals to run some very obvious malware.
The Lure
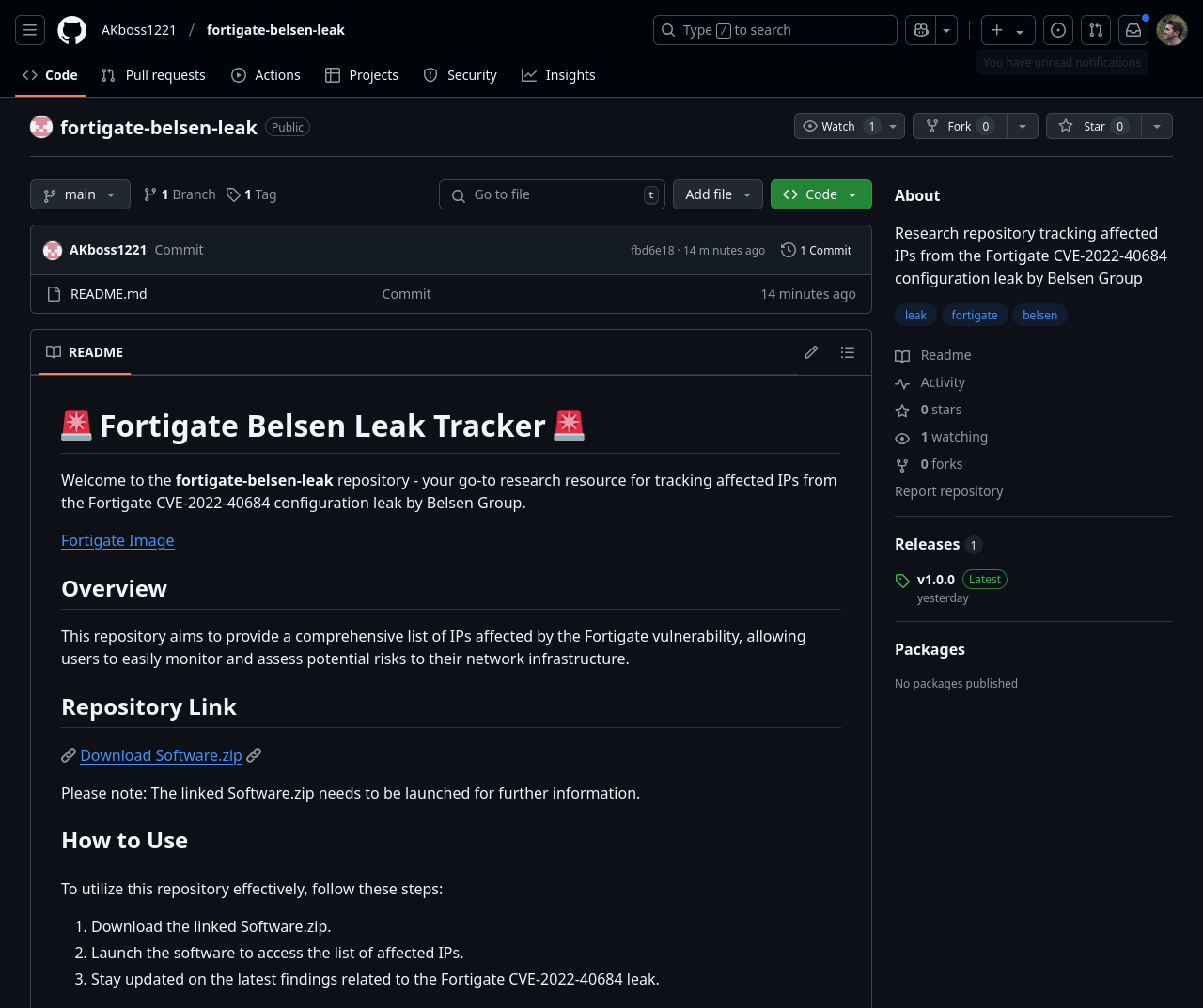
A GitHub user “AKboss1221” created a repository called “🚨 Fortigate Belsen Leak Tracker 🚨” in the hopes it would be picked up by search engines. Lucky for them, my search engine did, and I could see this horseshit.
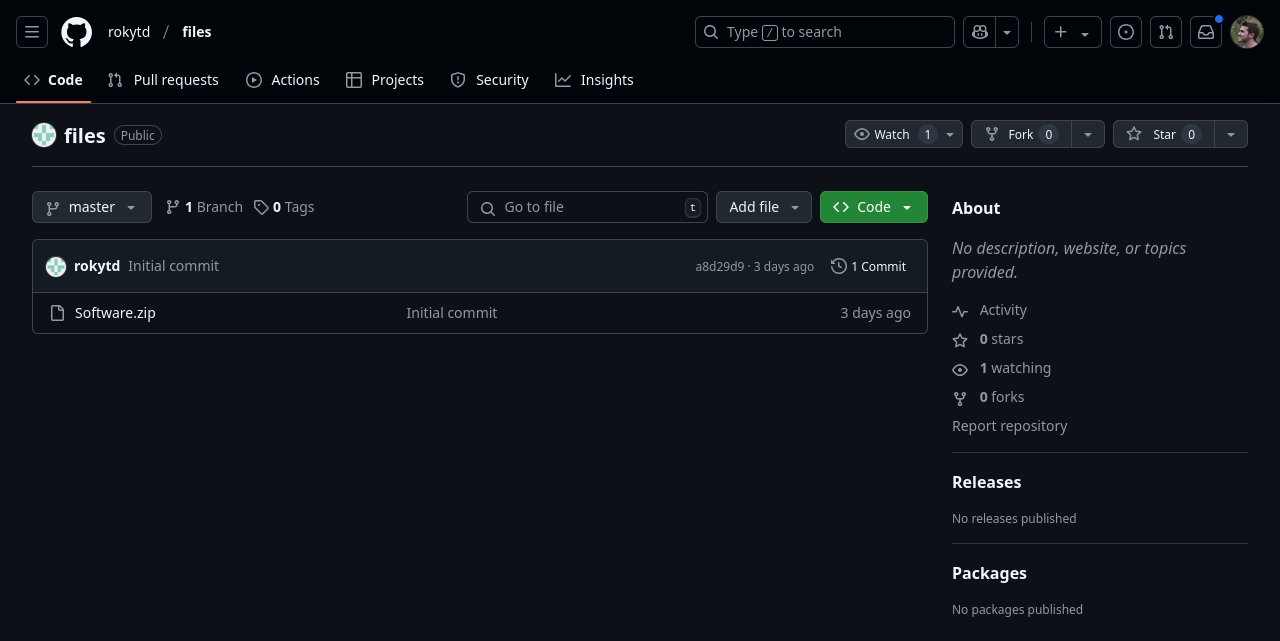
Apparently all we need to do to get our own copy is download and extract the Software.zip file (which is not in this repository, of course), and we’ll be provided with the list of affected IPs and “stay updated” about the leak. Wonderful. Let’s go get our copy of the malw– erm, leak, helpfully provided by user “rokytd” in their “files” repository.
The repos listed are the only public repos available in both AKboss1221 and rokytd’s GitHub accounts, so you can tell they are laser focused on distributing the highest quality FortiGate leaks and definitely not burner accounts serving malware. (screenshot of AKboss1221’s profile, screenshot of rokytd’s profile)
The Malware
Downloading the Software.zip file (VT, MalShare) and extracting it, we receive:
Software
├── config.txt
├── Launcher.bat
├── lua.exe
└── lua51.dll
Now, this is terrible news for me as a Linux user and AKboss1221 completely failed to mention there were platform limitations with their FortiGate leak distribution software, but I’m sure we can reverse engineer this to get our hands on that delicious FortiGate data.
Starting with the Launcher.bat file, we find:
start lua.exe config.txt
Which intends to run the bundled lua.exe (a Lua programming language interpreter) file on config.txt (VT, MalShare). Let’s check out that file next …
And hey, it’s obfuscated Lua. I’m feeling lazy since it’s the weekend, so let’s huck the whole thing into any.run and execute it to see what would happen. Immediately after opening Launcher.bat, we get alerts of malicious activity, as the Lua interpreter begins executing malware.
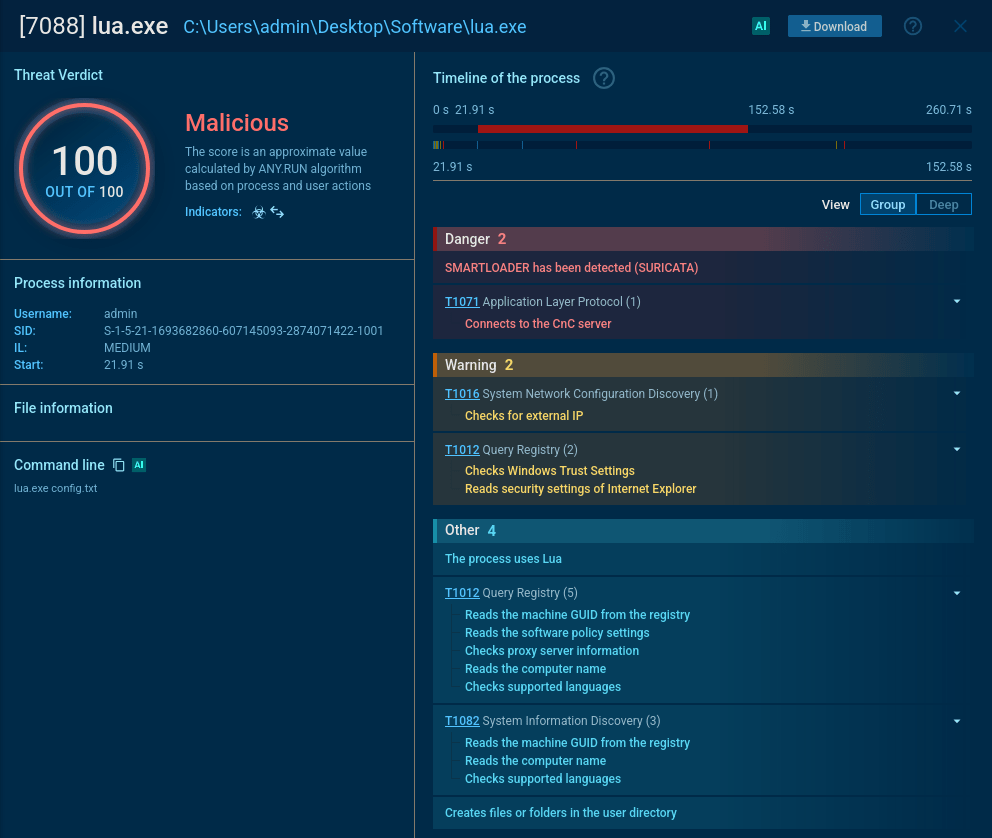
Network traffic shows we have a SmartLoader infection on our hands (Malpedia, MalwareBazaar) - SmartLoader is Lua malware, which has been doing the rounds since early 2024 after campaigns were discovered pushing SmartLoader in GitHub comments. SmartLoader has been often used to install infostealers such as Lumma, but the C&C servers that were connected to declined to serve me the next stage payload, likely as they noticed traffic was coming from a Tor exit node.
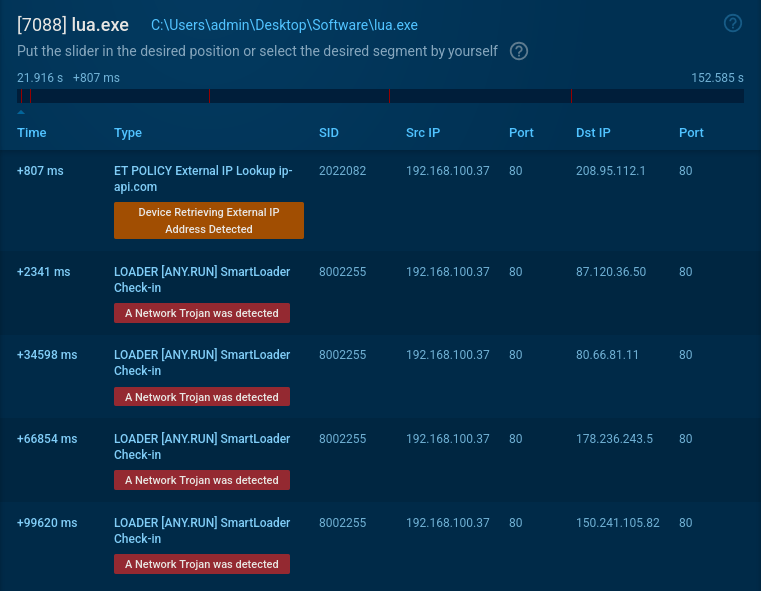 download PCAP of network activity
download PCAP of network activity
For your copy/paste convenience, the C&C severs observed in use above are:
87.120.36.50:8080.66.81.11:80178.236.243.5:80150.241.105.82:80
It would be reasonable to assume that this attacker would continue the stealer trend, as technoweenies have everything from cool credentials to cryptocurrency, both of which are a hot target. Though it seems threat actors aren’t getting any better at targeting InfoSec professionals since I last took a look at amateurish malware being posted on r/cybersecurity.
Conclusion
It seems that attackers are opportunistically targeting folks’ interest in the original file, as a lot of people are trying to download it with no success. Hopefully someone will get their hands on it and redistribute it, so it can be studied. Until then, I look forward to finding more interesting lures targeting InfoSec pros as … it’d be nice to take apart something new once in a while, you know?