In 2022, Russia began a full-scale invasion of Ukraine in the escalating Russo-Ukrainian war. Ukrainian ingenuity quickly led to the creation of a volunteer cyberwarfare organization, IT Army of Ukraine, which conducted both defensive and offensive operations. Notably, they invited anyone with an internet connection to DDoS an ever-growing list of Russian and Belarusian websites, with the goal of disrupting infrastructure and draining Russia’s own cyberwarfare capabilities.
I made a very quick project to assess the status of Russian and Belarusian internet properties (via RIPE Atlas) being targeted by hacktivists. Specifically, I evaluated almost every target listed by the IT ARMY Telegram group with many unique probes between 2022-02-27 (the day after IT ARMY was created) and 2022-05-30 to check for service availability.
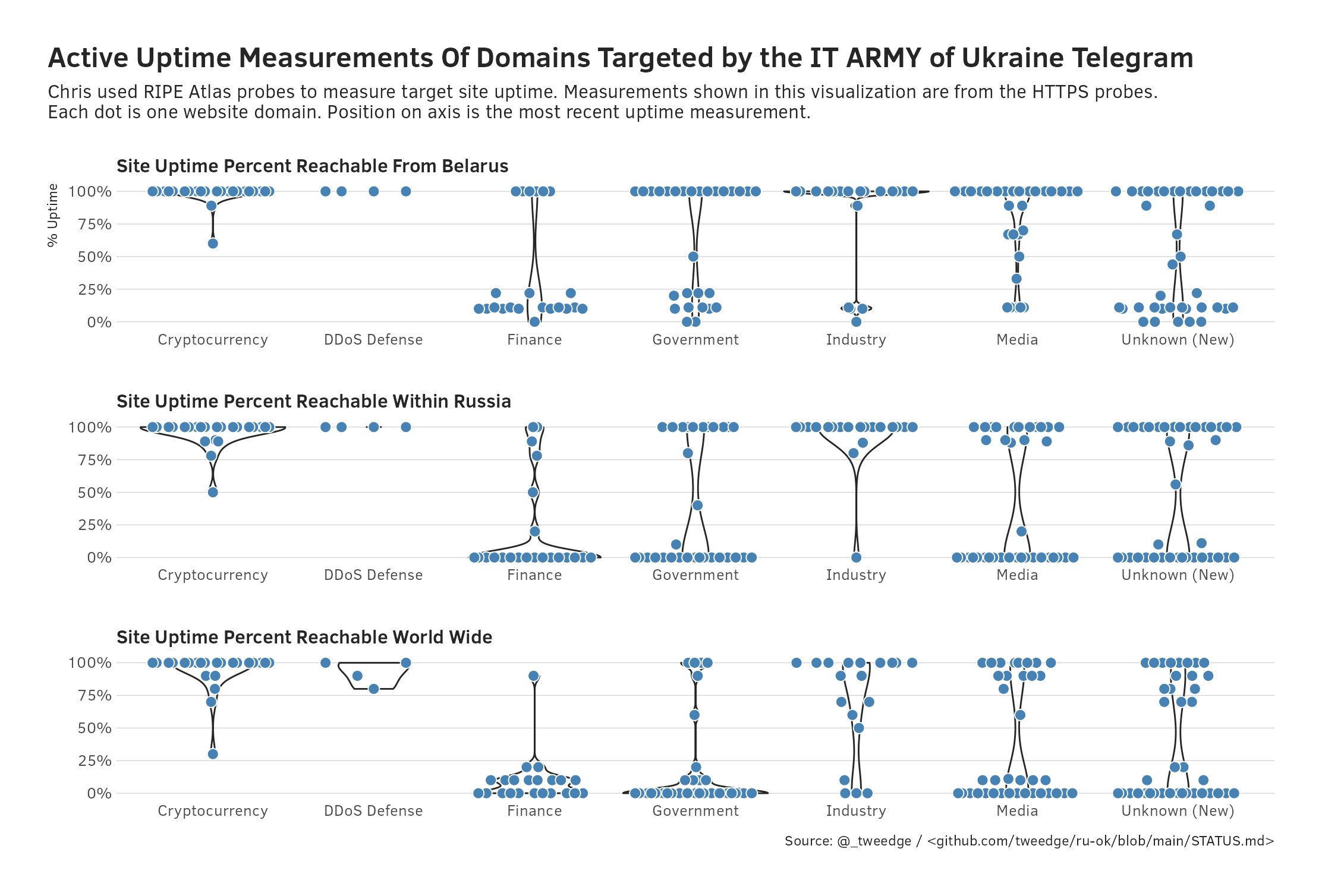
I wanted to check connectivity from within Russia’s borders because I saw many mixed reports across Twitter and Reddit, with international parties (Americans, Ukrainians, etc.) claiming many sites had been knocked offline, where Russians chimed in that many sites remained online for them. The truth is more complex - some sites were significantly disrupted and took time to recover glovally, while others had existing mitigations in place, others seemed to deprioritize or sinkhole international traffic, etc.
My research was included in several news articles around the world:
- Ukraine’s IT army is doing well, hitting Russia with ‘cost and chaos’ - VentureBeat
- Ukraine deserves an IT army. We have to live with the fallout - VentureBeat
- Ukraine: We’ve repelled ‘nonstop’ DDoS attacks from Russia - VentureBeat
- Guerre en Ukraine : les cyberattaques contre la Russie, le « cri de colère » d’une armée de volontaires - Le Monde
- Ukraine Demanded Cloudflare Stop Protecting Russians From Cyberattacks. Cloudflare Said No - Forbes
The data and methodology for RU-OK was originally published on my GitHub, where I hope it will remain. However, I’ve received the occasional nastygram about this research and recently received a takedown request against from a Russian cybersecurity firm, claiming that sensitive information is being stored in my repository. There isn’t, of course, and all the data is public measurements against public endpoints. Still I’m concerned that fraudulent reports could result in my repo getting deleted, so I’m creating a censorship-resistant copy and distributing it here and on Academic Torrents. It’s long overdue anyway.
I encourage anyone curious to take a dig through the data, as you can watch both the immediate impact of DDoS attacks as well as Russian government and company resilience change over several months as this attack became commonplace. As an example, hrbrmstr/boB Rudis charted uptime on 2022-03-03, showing different resilience against DDoS attacks by industry, as well as differences in how sites were accessible locally vs globally:
I hope you enjoy :)
Contents
This torrent contains an original, unmodified copy of all data I collected from 2022-02-27 to 2022-05-30, the final version of the scripts as of 2022-05-30 which I used to create all of the measurements and summarize day-by-day results, and an updated copy of the README. Unzipped, the total size is 14.2GB, and >99% of that is raw data.
File Tree Sample
The measurements are organized by:
- Every top level folder is a timestamp where I initiated measurements.
- Every subfolder is a distinct target listed by IT ARMY.
- Every subfolder within that is a distinct measurement ID which I initiated. There may be one or more measurement ID.
- Each measurement ID contains one
result.json, the raw measurement results from RIPE Atlas after all probes had completed the measurements.
% tree ru-ok
ru-ok
├── 2022-02-27-19:15:00
│ ├── alfaradio.by
│ │ └── 39083547
│ │ └── result.json
│ ├── api.developer.sber.ru
│ │ └── 39083526
│ │ └── result.json
│ ├── api.sberbank.ru
│ │ └── 39083527
│ │ └── result.json
... (continues for 91,646 more measurements)
├── collect_measurements.py
├── define_measurements.py
├── LICENSE
├── parse_measurements.py
├── README.md
├── run_measurements.py
├── STATUS.md
└── targets.json
The remaining files at the root are documentation and scripts I used to create all measurements.
Something that may be immediately useful to certain folks is that I hand-cataloged all 3,951 targets for DDoS attacks by IT ARMY from 2022-02-27 to 2022-05-30 as of when they were first targeted, and kept it updated daily. That was a labor of love and a pain in the ass. This is included in the original repo and archival torrent, but I’ve also included a copy of targets.json locally on my website as it’s relatively small. I did not include any field for when the target was most recently targeted, however, as IT ARMY did go back and re-name some existing targets for DDoS attacks throughout the months I was cataloging.
Example Measurement Data
The below sample from a result.json shows a single measurement against an IT ARMY target, alfaradio.by, which is not able to be accessed by a RIPE Atlas probe in Russia, due to a connection timeout. The probe is otherwise healthy and has a stable connection, which we can tell by the tags (ex. system: IPv4 Stable 30d). Additional data includes the exact timestamp when the measurement occurred, the user-reported coordinates of the probe, the probe’s IP address at the time of the measurement, etc. Each result.json is an array of multiple measurements like this.
[
{
"fw": 5040,
"mver": "2.4.1",
"lts": 4,
"dst_name": "alfaradio.by",
"dst_port": "443",
"ttr": 316.66766,
"dst_addr": "93.85.84.202",
"af": 4,
"err": "connect: timeout",
"msm_id": 39083547,
"prb_id": 1000860,
"timestamp": 1645989712,
"msm_name": "SSLCert",
"from": "91.122.46.136",
"type": "sslcert",
"group_id": 39083547,
"stored_timestamp": 1645989720,
"probe_data": {
"address_v4": "91.122.46.136",
"address_v6": null,
"asn_v4": 12389,
"asn_v6": null,
"country_code": "RU",
"description": "Akulich_Home",
"first_connected": 1597403630,
"geometry": {
"type": "Point",
"coordinates": [
30.4505,
60.0375
]
},
"id": 1000860,
"is_anchor": false,
"is_public": true,
"last_connected": 1645992489,
"prefix_v4": "91.122.0.0/17",
"prefix_v6": null,
"status": {
"id": 1,
"name": "Connected",
"since": "2022-02-23T00:13:05Z"
},
"status_since": 1645575185,
"tags": [
{
"name": "Fibre",
"slug": "fibre"
},
{
"name": "Home",
"slug": "home"
},
{
"name": "NAT",
"slug": "nat"
},
{
"name": "IPv4",
"slug": "ipv4"
},
{
"name": "system: Resolves AAAA Correctly",
"slug": "system-resolves-aaaa-correctly"
},
{
"name": "system: Resolves A Correctly",
"slug": "system-resolves-a-correctly"
},
{
"name": "system: Software",
"slug": "system-software"
},
{
"name": "system: IPv4 Capable",
"slug": "system-ipv4-capable"
},
{
"name": "system: IPv4 RFC1918",
"slug": "system-ipv4-rfc1918"
},
{
"name": "system: IPv4 Works",
"slug": "system-ipv4-works"
},
{
"name": "system: IPv4 Stable 1d",
"slug": "system-ipv4-stable-1d"
},
{
"name": "system: IPv4 Stable 30d",
"slug": "system-ipv4-stable-30d"
}
],
"total_uptime": 43963611,
"type": "Probe"
}
},
...
HTTPS Download
If you cannot use a torrent client, you can download ru-ok-2022-archive.zip from my GetRight server. However, I may limit the speed of these downloads to as little as 500KB/s due to cost - torrenting is a much more effective way to distribute data at scale, please prioritize it when possible.